Doc updated; added basic instructions for dev environment
This commit is contained in:
parent
257a53dfb8
commit
c4616aa5db
33
Readme.md
33
Readme.md
@ -145,9 +145,20 @@ It is important to note that in the last case, it is just a standard case of int
|
|||||||
|
|
||||||
|

|
||||||
|
|
||||||
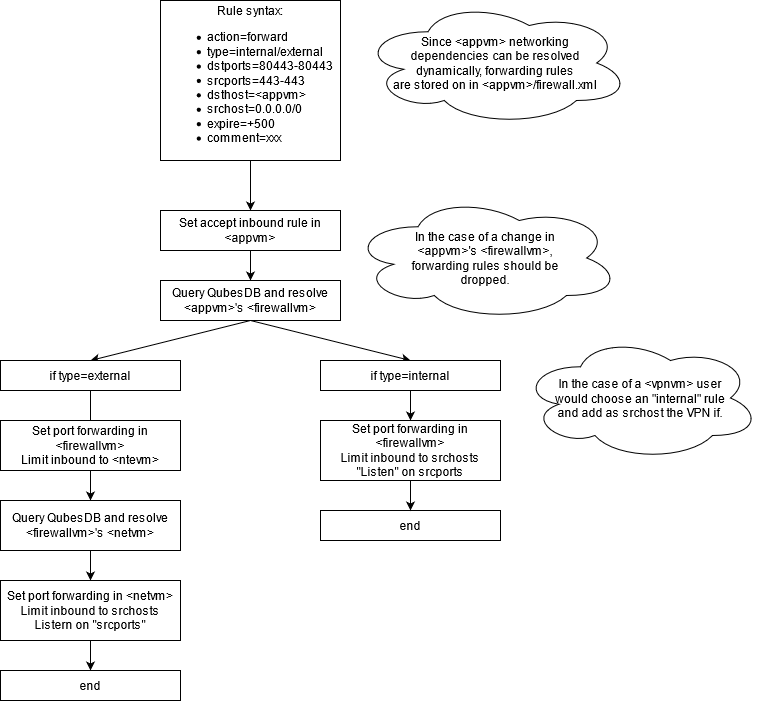
#### Implementation roadmap
|
### Implementation roadmap
|
||||||
|
|
||||||
|
|
||||||
|
1. ✔️ In `core-admin-client/qubesadmin/firewall.py` firewall.py > The code
|
||||||
|
needs to support the new options for the rule (action=forward
|
||||||
|
frowardtype=<internal/external> srcports=443-443 srchosts=0.0.0.0/0
|
||||||
|
2. ✔️ In `core-admin/qubes/firewall.py` -> The code needs to support the same
|
||||||
|
options as the point above
|
||||||
|
3. 🚧 In `core-admin/qubes/vm/mix/net.py` -> The most important logic goes
|
||||||
|
here. Here there is the need to resolve the full network chain for
|
||||||
|
external port forwarding. From here it is possible to add the respective
|
||||||
|
rules to the QubesDB of each NetVM in he chain and trigger a reload event.
|
||||||
|
4. ❌ In `core-agent-linux/qubesagent/firewall.py` -> Here goes the logic for
|
||||||
|
building the correct syntax for iptables or nft and the actual execution
|
||||||
|
5. ❌ GUI
|
||||||
|
|
||||||
### Required rules
|
### Required rules
|
||||||
|
|
||||||
@ -188,3 +199,21 @@ in `<appvm>`:
|
|||||||
```
|
```
|
||||||
iptables -w -I INPUT 5 -d <appvm_ip> -p tcp --dport <target_port> -m conntrack --ctstate NEW -j ACCEPT
|
iptables -w -I INPUT 5 -d <appvm_ip> -p tcp --dport <target_port> -m conntrack --ctstate NEW -j ACCEPT
|
||||||
```
|
```
|
||||||
|
|
||||||
|
## Extra
|
||||||
|
### Useful Commands
|
||||||
|
|
||||||
|
### Dev Environment
|
||||||
|
Currently developing on VMWare Workstation on Windows due to issues in virtualizing on linux on my home hardware.
|
||||||
|
QubesOS is virtualized behind NAT and can reach Windows Host via SSH.
|
||||||
|
|
||||||
|
In order to the the code, I wrote some [helper scripts](https://git.lsd.cat/Qubes/tools).
|
||||||
|
The required setup involves:
|
||||||
|
* Clone the tools on the Windows Host
|
||||||
|
* Generate an SSH keypair on `sys-net`
|
||||||
|
* Add `sys-net` SSH pubkey on Windows for non interactive authentication (`sshd` is easier using Windows Subsystem for Linux)
|
||||||
|
* Via scp/sftp, copy all the bash script in the `sys-net` VM. Leve `pull.sh` in `/home/user/pull.sh`
|
||||||
|
* Using `qvm-run` copy `backup.sh`, `restore.sh` and `updte.sh` in `Dom0`
|
||||||
|
* First, run once `backup.sh` and pay attention to never run it again in order to recover from broken states (breaking qubesd, `qvm-run` will stop working and it will be hard to recover)
|
||||||
|
* Run `update.sh` to automatically pull changes from the Windows host. `qubesd` is restarted within the same script.
|
||||||
|
* In case of issues, run `restore.sh` and investigate the previous errors
|
||||||
|
|||||||
Loading…
Reference in New Issue
Block a user