Lot of typos
This commit is contained in:
parent
1fbe8db87e
commit
3dea1e53d4
61
Readme.md
61
Readme.md
@ -6,8 +6,8 @@ Recently, some network devices caught my attention both on Aliexpress and Alibab
|
||||
* https://it.aliexpress.com/item/4000091742124.html
|
||||
* https://www.alibaba.com/product-detail/AR9331-long-range-wifi-192-168_62106638650.html
|
||||
|
||||
These are 2.4ghz AR9330 based boards, powered via POE (although on a non standard voltage), with two 10/100/1000 ethernet ports, an integrated antenna and a waterproof enclosure.
|
||||
I received the first one from Aliexpress but i plan to get some other to test as well.
|
||||
These are 2.4ghz AR9330 based boards, powered via POE (although on a nonstandard voltage), with two 10/100/1000 Ethernet ports, an integrated antenna, and a waterproof enclosure.
|
||||
I received the first one from Aliexpress but I plan to get some other to test as well.
|
||||
|
||||
[There's a video on YouTube of someone unpacking and reviewing it](https://www.youtube.com/watch?v=i3WUmMOqit0). It also shows the OEM web interface.
|
||||
|
||||
@ -22,8 +22,8 @@ From the PCB picture it is clear that the board has an easily accessible serial
|
||||
|
||||
## Dumping firmware
|
||||
### Dumping the original firmware without hardware
|
||||
Before even trying the SOIC clip or the serial port i wanted to check around the stock firmware. It looks like the device has no DHCP server but it has a fixed `192.168.0.1` ip address and default `admin:admin` credentials.
|
||||
By default, there's only the web intrace and a telnet server listening on the public interface. The credentials for the telnet interface are `root` without password.
|
||||
Before even trying the SOIC clip or the serial port I wanted to check around the stock firmware. It looks like the device has no DHCP server but it has a fixed `192.168.0.1` IP address and default `admin:admin` credentials.
|
||||
By default, there's only the web interface and a telnet server listening on the public interface. The credentials for the telnet interface are `root` without a password.
|
||||
|
||||
```
|
||||
CPE46B mips #1 Thu Sep 5 18:02:48 CST 2019 (none)
|
||||
@ -60,7 +60,7 @@ Interactive mode
|
||||
>
|
||||
```
|
||||
|
||||
While upon collecting the user is dropped in a restriced pompt with few commands available, it is possible to inject commands in almost any of it via common shell separators `|;&`.
|
||||
While upon collecting the user is dropped in a restricted prompt with few commands available, it is possible to inject commands in almost any of it via common shell separators `|;&`.
|
||||
With the command injection is easy to understand that the device is already running a heavily customized OpenWrt fork, running on `Linux 2.6.31`.
|
||||
|
||||
```
|
||||
@ -78,7 +78,7 @@ br0 no wireless extensions.
|
||||
Linux CPE46B 2.6.31--LSDK-9.2.0_U9.915 #1 Thu Sep 5 18:02:48 CST 2019 mips GNU/Linux
|
||||
```
|
||||
|
||||
Catting `/proc/mtd` gives more info about flash layout.
|
||||
Catting `/proc/mtd` gives more info about the flash layout.
|
||||
|
||||
|
||||
```
|
||||
@ -115,7 +115,7 @@ VCEI exceptions : not available
|
||||
|
||||
By knowing the size of each mtd partition, we get to know that it has a 8MiB flash chip. This makes sense given that the chip has written on it `25Q64`, where `64` is the size in Megabits.
|
||||
|
||||
Using `dd` it is possible to dump each partition, download it and even reasseble the full firmware image simply with `cat` afterwards.
|
||||
Using `dd` it is possible to dump each partition, download it and even reassemble the full firmware image simply with `cat` afterwards.
|
||||
|
||||
|
||||
for X in 0..6
|
||||
@ -142,10 +142,10 @@ Also do a `sha1sum` of the final file. It should match the image extracted later
|
||||
|
||||
Where `8388608/1024=8192K`.
|
||||
|
||||
When the device boots up, a lot of custom scripts and services will run. The most custom part of the firmware, which means the web interface and their custom binaries are somehow encrypted or more simply obfuscated and loaded at runtime in ram. At rest, the obfuscated files are called `/usr/web.bin`, `/usr/sbin.bin`, `/usr/apps.bin`. The executable responsabile for decrypting them to more simpler `tgz` archives is called `ap_monitor`. Ghidra sucessfully decompile this binary and the obfuscation mechanism is not very complicated and could reversed with not too much effort but there's proably no reason to do so.
|
||||
When the device boots up, a lot of custom scripts and services will run. The most custom part of the firmware, which means the web interface and their custom binaries are somehow encrypted or more simply obfuscated and loaded at runtime in ram. At rest, the obfuscated files are called `/usr/web.bin`, `/usr/sbin.bin`, `/usr/apps.bin`. The executable responsible for decrypting them to more simpler `tgz` archives is called `ap_monitor`. Ghidra successfully decompile this binary and the obfuscation mechanism is not very complicated and could be reversed with not too much effort but there's probably no reason to do so.
|
||||
|
||||
|
||||
Since I was unable to find the manufacturer both on the package or anywhere else, i'll refer to it as `ZiKing` as it seems that's the name stated in their own proprietary config file. On Aliexpress, the same device is also often said to be made by `ANDDEAR`. Both do not seem to have any presence on the English internet.
|
||||
Since I was unable to find the manufacturer both on the package or anywhere else, I'll refer to it as `ZiKing` as it seems that's the name stated in their own proprietary config file. On Aliexpress, the same device is also often said to be made by `ANDDEAR`. Both do not seem to have any presence on the English internet.
|
||||
|
||||
```
|
||||
FID="OEM"
|
||||
@ -224,9 +224,9 @@ The only thing actually existing, given that as of now the website shows a defau
|
||||
|
||||
|
||||
|
||||
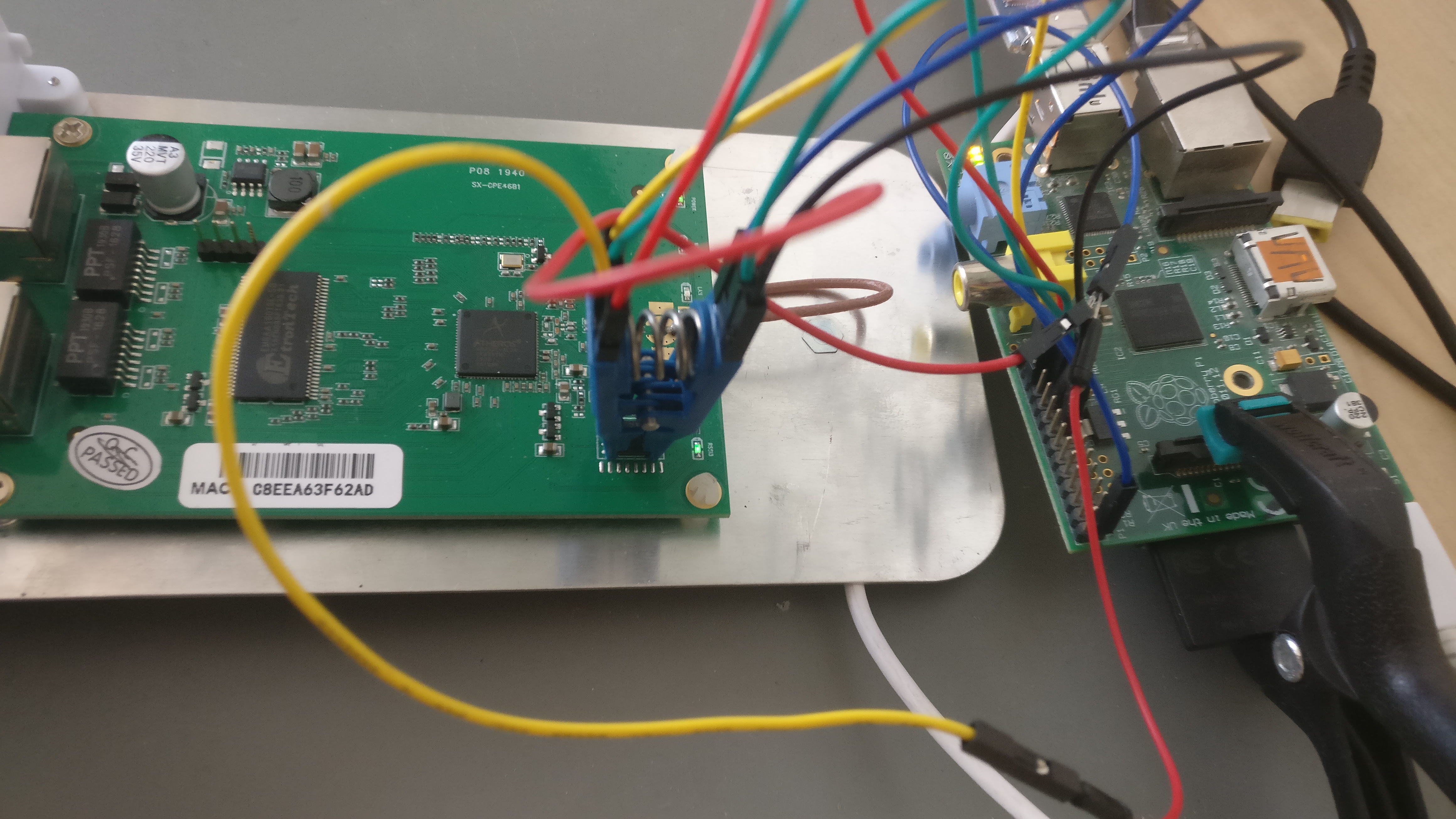
[The following istruction are recycled from this other guide](https://git.lsd.cat/g/thinkpad-coreboot-qubes/src/master/README.md).
|
||||
[The following instructions are recycled from this other guide](https://git.lsd.cat/g/thinkpad-coreboot-qubes/src/master/README.md).
|
||||
|
||||
_WARNING: The Raspberry VCC will five some power also to the SoC. This means that there might be interference given the unknown state of the SoC while wotking on the flash chip. In my case, that lead to some verifying errors after a write, but the write itself never failed._
|
||||
_WARNING: The Raspberry VCC will five some power also to the SoC. This means that there might be interference given the unknown state of the SoC while working on the flash chip. In my case, that lead to some verifying errors after a write, but the write itself never failed._
|
||||
|
||||
```
|
||||
______
|
||||
@ -237,7 +237,7 @@ _WARNING: The Raspberry VCC will five some power also to the SoC. This means tha
|
||||
|
||||
```
|
||||
|
||||
Remeber to research your chip model and manufacturer and double check the pin layout using the official datasheet.
|
||||
Remember to research your chip model and manufacturer and double-check the pin layout using the official datasheet.
|
||||
|
||||
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | Flash pin number |
|
||||
|----|----|-----|-----|----|-----|-------|-----|------------------|
|
||||
@ -268,9 +268,9 @@ For more information about In-System Programming, [visit the flashrom wiki](http
|
||||
|
||||
|
||||
|
||||
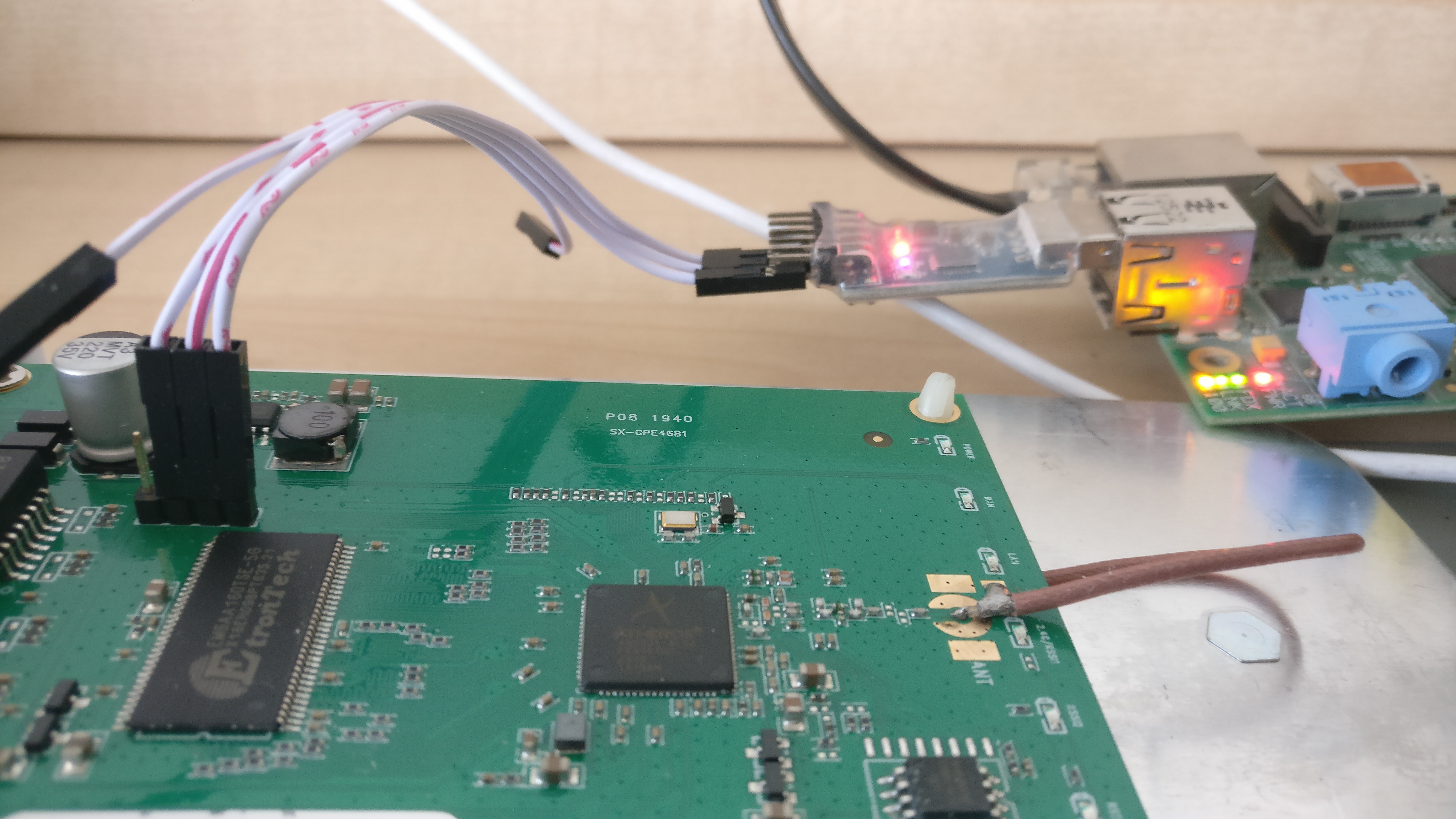
The serial header is easy to work with and has clearly written the pinout on it. Any cheap usb adapter will probably work. In my case the baudrate is 115200, however, a script like [baudare.py](https://github.com/somu1795/baudrate) should do the trick.
|
||||
The serial header is easy to work with and has clearly written the pinout on it. Any cheap USB adapter will probably work. In my case the baud rate is 115200, however, a script like [baudare.py](https://github.com/somu1795/baudrate) should do the trick.
|
||||
|
||||
Common softwares for serial communication are `minicom` and `screen`.
|
||||
Common software for serial communication are `minicom` and `screen`.
|
||||
|
||||
```
|
||||
# screen /dev/ttyUSB0 115200
|
||||
@ -289,13 +289,13 @@ The info learnt from `/proc/mtd` are extremely useful.
|
||||
* `mtd5 NVRAM` is a 64KiB partition which contains a `tgz` for OEM system configuration files
|
||||
* `mtd6 ART` is a 64KiB partition [that contains calibration data for the radio chip](https://github.com/pepe2k/ar9300_eeprom)
|
||||
|
||||
The total size is of course 8192KiB. The partitions are not partitions in an EXT or NTFS sense. The data is just contiguos on the flash but the bootloader and the kernel are responsible for considering the different regions separate.
|
||||
The total size is of course 8192KiB. The partitions are not partitions in an EXT or NTFS sense. The data is just contiguous on the flash but the bootloader and the kernel are responsible for considering the different regions separate.
|
||||
|
||||
That's the reason because `cat` works and it is so simple to work with them.
|
||||
|
||||
Since for vanilla OpenWrt a custom partition for configuration is not needed, and two rootfs aren't useful and everything can be packed in a single partition with more space for packages and user data our target could be:
|
||||
|
||||
* `mtd0 u-boot` oeiginal image
|
||||
* `mtd0 u-boot` original image
|
||||
* `mtd1 u-boot-env` some values here needs to be modified
|
||||
* `mtd2 firmware` 8000K OpenWrt partition (`firmware` is the standard OpenWrt naming)
|
||||
* `mtd3 ART` original image
|
||||
@ -451,10 +451,10 @@ Environment size: 978/65532 bytes
|
||||
|
||||
The same information can be obtained by running `strings` on the `mtd1` partition image.
|
||||
|
||||
As seen above, the `bootargs` variable contains the serial console information, the partition scheme and the init information. So any change in the partition scheme must be reflected in this variable.
|
||||
The other important value is `bootcmd`: it cointains the actual boot command. The address there is the starting address of the partition that contains the kernel image (with a `0x9f` prefix).
|
||||
As seen above, the `bootargs` variable contains the serial console information, the partition scheme, and the init information. So any change in the partition scheme must be reflected in this variable.
|
||||
The other important value is `bootcmd`: it contains the actual boot command. The address there is the starting address of the partition that contains the kernel image (with a `0x9f` prefix).
|
||||
|
||||
So, given 0x0038000 which is `3670016/1024=3584KiB`. So by summing up the size of `mtd0`, `mtd1`, and `mtd2` the total should be the `mtd3` startign address: `64+64+3456=3584KiB`.
|
||||
So, given 0x0038000 which is `3670016/1024=3584KiB`. So by summing up the size of `mtd0`, `mtd1`, and `mtd2` the total should be the `mtd3` starting address: `64+64+3456=3584KiB`.
|
||||
|
||||
So while we don't have our OpenWrt image yet, let's try to write the new variables for the new partition scheme described in the previous section:
|
||||
|
||||
@ -465,6 +465,15 @@ bootcmd=bootm 0x9f020000
|
||||
|
||||
Where, `root=31:02` stands for the `mtd2` partition which is labelled `firmware`. The `bootcmd` address is `0x0002000` which is 128KiB. `8000k` is the OpenWrt partition size.
|
||||
|
||||
However, it looks like now the `root` and `mtdparts` parameters are no longer needed since the DTS is built into the image (more on this later). Also, the default init for OpenWrt is `/sbin/init` so that may be omitted too.
|
||||
|
||||
The following environment should be sufficient:
|
||||
```
|
||||
bootargs=console=ttyS0,115200 rootfstype=squashfs,jffs2
|
||||
bootcmd=bootm 0x9f020000
|
||||
```
|
||||
|
||||
|
||||
#### Changing u-boot environment
|
||||
U-boot ships also with the commands `setenv` and `saveenv`. The first one will change or add a variable in the current session, the second one will write the current state on the u-boot-env partition.
|
||||
|
||||
@ -511,7 +520,7 @@ Environment size: 498/65532 bytes
|
||||
```
|
||||
|
||||
##### Warning
|
||||
The following methos has not worked with me, but I'm documenting it anyway.
|
||||
The following method has not worked with me, but I'm documenting it anyway.
|
||||
|
||||
As for the u-boot environment, it is possible to create an entirely new `u-boot-env` data using an utility called `mkenvimage` which is shipped within the u-boot source.
|
||||
Simply write all the parameters in a file called `env.txt`
|
||||
@ -551,9 +560,9 @@ So what need to be done is:
|
||||
* Find out led and button GPIO
|
||||
* Add additional board specific files (for network, calibration, etc)
|
||||
|
||||
One of the best way to understand the process is to look at recent commits that add supports for some device, especially if with the same SoC. As an example reference, I used the [Comfast CF-EW72 target](https://git.openwrt.org/?p=openwrt/openwrt.git;a=commit;h=7daab6286110b95167e291409395494f18edc9dc).
|
||||
One of the best ways to understand the process is to look at recent commits that add supports for some device, especially if with the same SoC. As an example reference, I used the [Comfast CF-EW72 target](https://git.openwrt.org/?p=openwrt/openwrt.git;a=commit;h=7daab6286110b95167e291409395494f18edc9dc).
|
||||
|
||||
I copied a DTS of the same SoC, specifically `./target/linux/ath79/dts/ar9330_glinet_gl-ar150.dts` in the OpenWrt source tree, adjusted the partition scheme, removed the GPIO info that i don't have yet, checked that the ART partition offsets do match with mine. Here's the result:
|
||||
I copied a DTS of the same SoC, specifically `./target/linux/ath79/dts/ar9330_glinet_gl-ar150.dts` in the OpenWrt source tree, adjusted the partition scheme, removed the GPIO info that I don't have yet, checked that the ART partition offsets do match with mine. Here's the result:
|
||||
|
||||
```
|
||||
// SPDX-License-Identifier: GPL-2.0-or-later OR MIT
|
||||
@ -646,7 +655,7 @@ I copied a DTS of the same SoC, specifically `./target/linux/ath79/dts/ar9330_gl
|
||||
};
|
||||
```
|
||||
|
||||
Futhermore, i added the `ZiKing CPE46B` target in order to be able to select the target image using OpenWrt build system.
|
||||
Futhermore, I added the `ZiKing CPE46B` target in order to be able to select the target image using OpenWrt build system.
|
||||
|
||||
In the file `./target/linux/ath79/image/generic.mk` add:
|
||||
|
||||
@ -661,7 +670,7 @@ endef
|
||||
TARGET_DEVICES += ziking_cpe46b
|
||||
```
|
||||
|
||||
`8000k` is the size of the partition we decided before. It should be now possible to select the new target using the standard `make menuconfig` and following normal OpenWrt build instructions.
|
||||
`8000k` is the size of the partition chosen before. It should be now possible to select the new target using the standard `make menuconfig` and following normal OpenWrt build instructions.
|
||||
|
||||
The result should be the file called `./bin/targets/ath79/generic/openwrt-ath79-generic-ziking_cpe46b-squashfs-sysupgrade.bin`
|
||||
|
||||
@ -728,7 +737,7 @@ Verifying flash... VERIFIED.
|
||||
```
|
||||
|
||||
## Reboot!
|
||||
Now it is possible to reboot the device and hope everything has worked as expected. While the serial console is still useful in order to see the boot process, the debug messages and eventual problems, OpenWrt will now work normally and it is possible to connect via thernet and get an IP Address assigned (by default there's `odhcpd` running).
|
||||
Now it is possible to reboot the device and hope everything has worked as expected. While the serial console is still useful in order to see the boot process, the debug messages and eventual problems, OpenWrt will now work normally and it is possible to connect via ethernet and get an IP Address assigned (by default there's `odhcpd` running).
|
||||
|
||||
```
|
||||
BusyBox v1.31.1 () built-in shell (ash)
|
||||
@ -754,7 +763,7 @@ Linux OpenWrt 4.19.108 #0 Mon Apr 13 08:14:48 2020 mips GNU/Linux
|
||||
|
||||
`#openwrt-devel` on `irc.freenode.net` has been very helpful. The channel is well populated and people try to do their best to answer technical questions.
|
||||
|
||||
A special thanks to _Paul Fertser_, (`PaulFertser` on `irc.freenode.net`)
|
||||
A special thanks to _Paul Fertser_ (`PaulFertser` on `irc.freenode.net`)
|
||||
|
||||
## TODO
|
||||
|
||||
|
||||
Loading…
Reference in New Issue
Block a user