Writed online flash dumping
This commit is contained in:
parent
91f3286b39
commit
a8aef9d72c
99
Readme.md
99
Readme.md
@ -24,16 +24,109 @@ From the PCB picture it is clear that the board has an easily accessible serial
|
||||
Before even trying the SOIC clip or the serial port i wanted to check around the stock firmware. It looks like the device has no DHCP server but it has a fixed `192.168.0.1` ip address and default `admin:admin` credentials.
|
||||
By default, there's only the web intrace and a telnet server listening on the public interface. The credentials for the telnet interface are `root` without password.
|
||||
|
||||
```
|
||||
CPE46B mips #1 Thu Sep 5 18:02:48 CST 2019 (none)
|
||||
CPE46B login: root
|
||||
Ziking logintalk start ...................
|
||||
|
||||
|
||||
|
||||
|
||||
Interactive mode
|
||||
|
||||
> ?
|
||||
Unknown command '?'
|
||||
help :Show this usage help
|
||||
art.sh :Run art server
|
||||
get_log :Download log from ap to remote. Usage: get_log [remote ip]
|
||||
ifconfig :Network configuration commands
|
||||
ip :Network configuration commands
|
||||
iwconfig :Wlan configuration commands
|
||||
iwpriv :Wlan configuration commands
|
||||
iwlist :Wlan configuration commands
|
||||
oem :Change/Show MAC address & sn; Usage: oem get/set
|
||||
ping :Command ping
|
||||
ps :Command ps
|
||||
route :Network configuration commands
|
||||
sendAT :Send AT command for lte device
|
||||
show_oem :Show OEM infomation
|
||||
show_ver :Show AP software version
|
||||
tc :Qos configuration commands
|
||||
top :Command top
|
||||
wlanconfig :Athreos wlan configuration commands
|
||||
T1 :Test 5G RF with 20M bandwidth
|
||||
T2 :Test 5G RF with 40M bandwidth
|
||||
T3 :Test 2.4G RF with 20M bandwidth
|
||||
T4 :Test 2.4G RF with 40M bandwidth
|
||||
T5 :Test upload.Usage: T5 [remote ip]
|
||||
T6 :Test download.Usage: T6
|
||||
>
|
||||
```
|
||||
|
||||
While upon collecting the user is dropped in a restriced pompt with few commands available, it is possible to inject commands in almost any of it via common shell separators `|;&`.
|
||||
With the command injection is easy to understand that the device is already running a heavily customized OpenWRT fork, running on `Linux 2.6.31`.
|
||||
|
||||
Catting `/proc/self/cmdline` gives more info about the boot command.
|
||||
```
|
||||
> iwconfig|uname -a
|
||||
lo no wireless extensions.
|
||||
|
||||
eth0 no wireless extensions.
|
||||
|
||||
eth1 no wireless extensions.
|
||||
|
||||
wifi0 no wireless extensions.
|
||||
|
||||
br0 no wireless extensions.
|
||||
|
||||
Linux CPE46B 2.6.31--LSDK-9.2.0_U9.915 #1 Thu Sep 5 18:02:48 CST 2019 mips GNU/Linux
|
||||
```
|
||||
|
||||
Catting `/proc/mtd` gives more info about flash layout.
|
||||
|
||||
|
||||
```
|
||||
|
||||
> iwconfig|cat /proc/mtd
|
||||
dev: size erasesize name
|
||||
mtd0: 00010000 00010000 "u-boot"
|
||||
mtd1: 00010000 00010000 "u-boot-env"
|
||||
mtd2: 00360000 00010000 "rootfs"
|
||||
mtd3: 00100000 00010000 "uImage"
|
||||
mtd4: 00360000 00010000 "rootfs1"
|
||||
mtd5: 00010000 00010000 "NVRAM"
|
||||
mtd6: 00010000 00010000 "ART"
|
||||
```
|
||||
|
||||
By knowing the size of each mtd partition, we get to know that it has a 8M flash chip. This makes sense given that the chip has written on it `25Q64`, where `64` is the size in Megabits.
|
||||
|
||||
Using `dd` it is possible to dump each partition, download it and even reasseble the full firmware image simply with `cat` afterwards.
|
||||
|
||||
|
||||
for X in 0..5
|
||||
```
|
||||
> iwconfig|dd if=/dev/mtd0 of=/var/tmp/web/mtdX
|
||||
```
|
||||
|
||||
for X in 0..5
|
||||
```
|
||||
# wget http://192.168.0.0.1/mtdX
|
||||
```
|
||||
|
||||
```
|
||||
# cat mtd0 mtd1 mtd2 mtd3 mtd4 mtd5 mtd6 > flash.bin
|
||||
```
|
||||
|
||||
```
|
||||
# ls -lart flash.bin
|
||||
-rwxrwxrwx 1 user user 8388608 Apr 12 12:40 flash.bin
|
||||
```
|
||||
|
||||
Where `8388608/1024=8192K`.
|
||||
|
||||
When the device boots up, a lot of custom scripts and services will run. The most custom part of the firmware, which means the web interface and their custom binaries are somehow encrypted or more simply obfuscated and loaded at runtime in ram. At rest, the obfuscated files are called `/usr/web.bin`, `/usr/sbin.bin`, `/usr/apps.bin`. The executable responsabile for decrypting them to more simpler `tgz` archives is called `ap_monitor`. Ghidra sucessfully decompile this binary and the obfuscation mechanism is not very complicated and could reversed with not too much effort but there's proably no reason to do so.
|
||||
|
||||
|
||||
|
||||
The
|
||||
|
||||
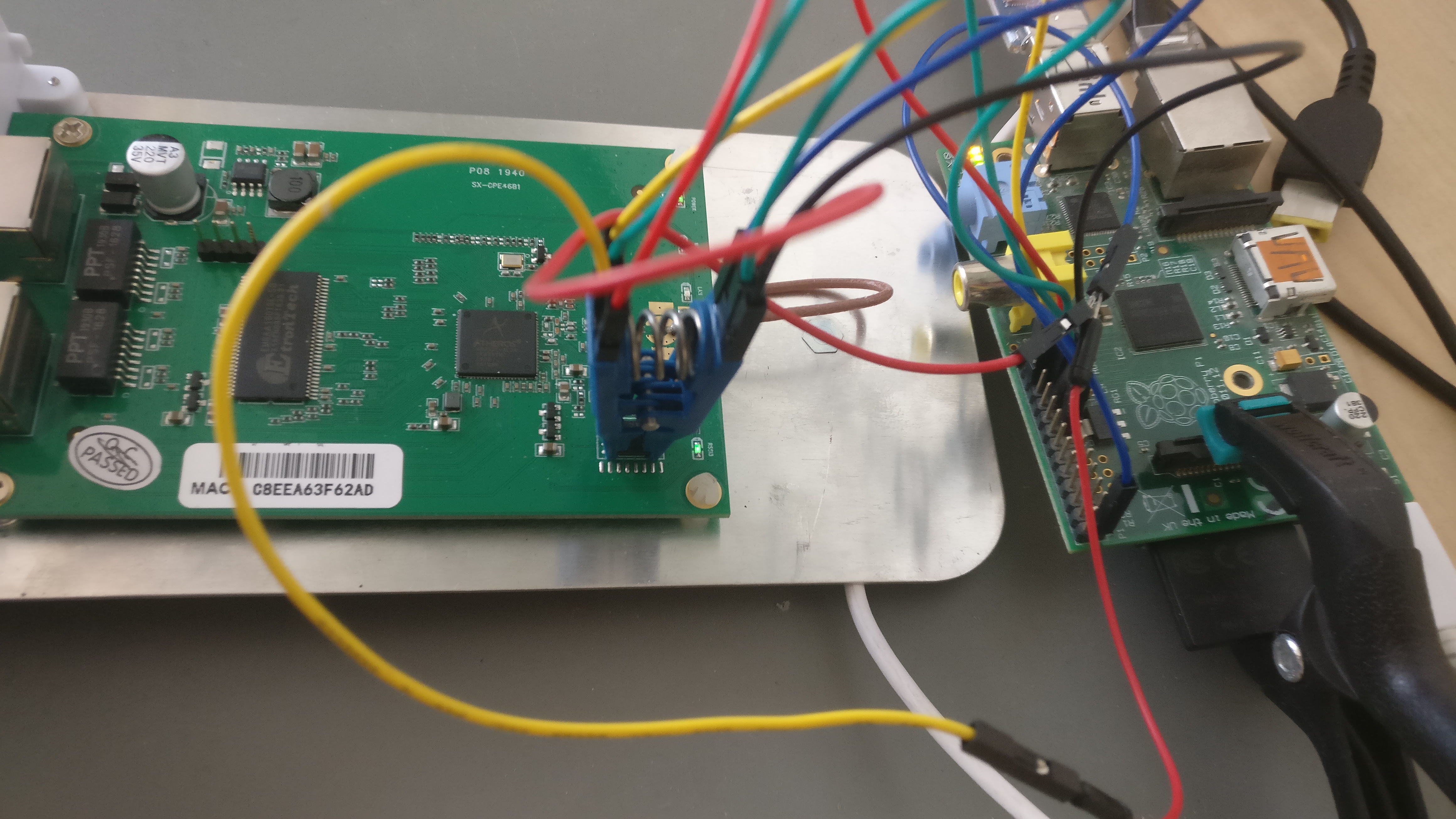
## Raspberry PI GPIO with a SOIC8 CLIP
|
||||
|
||||
@ -76,7 +169,7 @@ Check that all the checksums do match. In case they don't there's probably somet
|
||||
|
||||
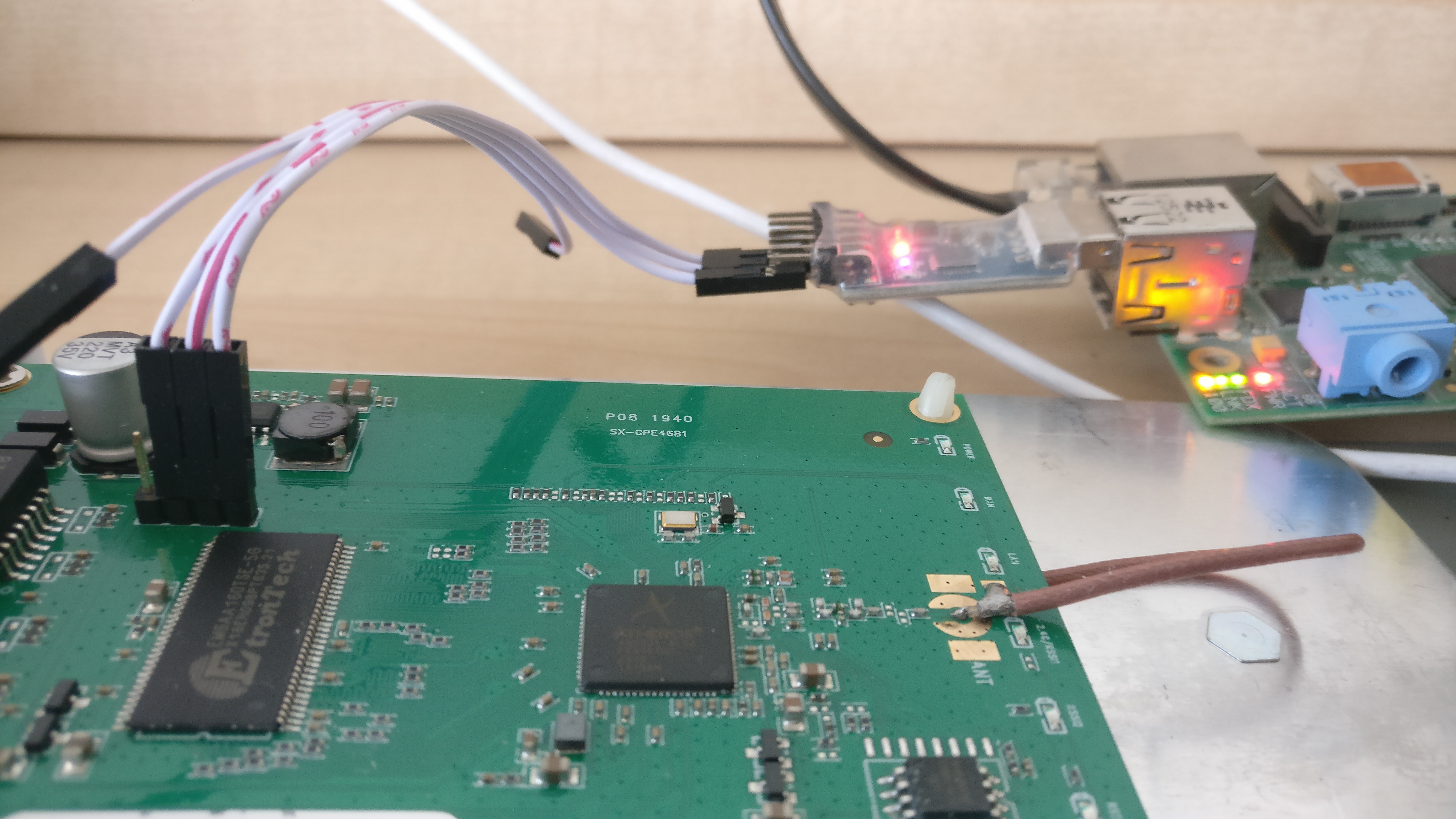
## Serial interface
|
||||
|
||||
|
||||
|
||||
|
||||
The serial header is easy to work with and has clearly written the pinout on it. Any cheap usb adapter will probably work. In my case the baudrate is 115200, however, a script like [baudare.py](https://github.com/somu1795/baudrate) should do the trick.
|
||||
|
||||
|
||||
Loading…
Reference in New Issue
Block a user