MTD sections
This commit is contained in:
parent
a8aef9d72c
commit
d607958415
152
Readme.md
152
Readme.md
@ -2,9 +2,9 @@
|
||||
## Intro
|
||||
Recently, some network devices caught my attention both on Aliexpress and Alibaba. Specifically, I found some interesting outdoor equipment for a very low price, ranging between 10-25$.
|
||||
|
||||
https://it.aliexpress.com/item/32964460654.html
|
||||
https://it.aliexpress.com/item/4000091742124.html
|
||||
https://www.alibaba.com/product-detail/AR9331-long-range-wifi-192-168_62106638650.html
|
||||
* https://it.aliexpress.com/item/32964460654.html
|
||||
* https://it.aliexpress.com/item/4000091742124.html
|
||||
* https://www.alibaba.com/product-detail/AR9331-long-range-wifi-192-168_62106638650.html
|
||||
|
||||
These are 2.4ghz AR9330 based boards, powered via POE (although on a non standard voltage), with two 10/100/1000 ethernet ports, an integrated antenna and a waterproof enclosure.
|
||||
I received the first one from Aliexpress but i plan to get some other to test as well.
|
||||
@ -20,7 +20,8 @@ I received the first one from Aliexpress but i plan to get some other to test as
|
||||
## PCB
|
||||
From the PCB picture it is clear that the board has an easily accessible serial header and that it has a SOIC8 flash chip (Winbond 25Q64). Given this info, there are two possibilities to start learning about the board via hardware: connecting to the serial console and get whatever the oem firmware prints out and do a direct hardware image of the flash chip.
|
||||
|
||||
## Dumping the original firmware without hardware
|
||||
## Dumping firmware
|
||||
### Dumping the original firmware without hardware
|
||||
Before even trying the SOIC clip or the serial port i wanted to check around the stock firmware. It looks like the device has no DHCP server but it has a fixed `192.168.0.1` ip address and default `admin:admin` credentials.
|
||||
By default, there's only the web intrace and a telnet server listening on the public interface. The credentials for the telnet interface are `root` without password.
|
||||
|
||||
@ -29,13 +30,9 @@ By default, there's only the web intrace and a telnet server listening on the pu
|
||||
CPE46B login: root
|
||||
Ziking logintalk start ...................
|
||||
|
||||
|
||||
|
||||
|
||||
Interactive mode
|
||||
|
||||
> ?
|
||||
Unknown command '?'
|
||||
> help
|
||||
help :Show this usage help
|
||||
art.sh :Run art server
|
||||
get_log :Download log from ap to remote. Usage: get_log [remote ip]
|
||||
@ -96,19 +93,39 @@ mtd5: 00010000 00010000 "NVRAM"
|
||||
mtd6: 00010000 00010000 "ART"
|
||||
```
|
||||
|
||||
And `/proc/cpuinfo` about the SoC and the CPU.
|
||||
|
||||
```
|
||||
> iwconfig|cat /proc/cpuinfo
|
||||
system type : Atheros AR9330 (Hornet)
|
||||
processor : 0
|
||||
cpu model : MIPS 24Kc V7.4
|
||||
BogoMIPS : 266.24
|
||||
wait instruction : yes
|
||||
microsecond timers : yes
|
||||
tlb_entries : 16
|
||||
extra interrupt vector : yes
|
||||
hardware watchpoint : yes, count: 4, address/irw mask: [0x0000, 0x0020, 0x0020, 0x0588]
|
||||
ASEs implemented : mips16
|
||||
shadow register sets : 1
|
||||
core : 0
|
||||
VCED exceptions : not available
|
||||
VCEI exceptions : not available
|
||||
```
|
||||
|
||||
By knowing the size of each mtd partition, we get to know that it has a 8M flash chip. This makes sense given that the chip has written on it `25Q64`, where `64` is the size in Megabits.
|
||||
|
||||
Using `dd` it is possible to dump each partition, download it and even reasseble the full firmware image simply with `cat` afterwards.
|
||||
|
||||
|
||||
for X in 0..5
|
||||
for X in 0..6
|
||||
```
|
||||
> iwconfig|dd if=/dev/mtd0 of=/var/tmp/web/mtdX
|
||||
```
|
||||
|
||||
for X in 0..5
|
||||
for X in 0..6
|
||||
```
|
||||
# wget http://192.168.0.0.1/mtdX
|
||||
# wget http://192.168.0.1/mtdX
|
||||
```
|
||||
|
||||
```
|
||||
@ -125,10 +142,82 @@ Where `8388608/1024=8192K`.
|
||||
When the device boots up, a lot of custom scripts and services will run. The most custom part of the firmware, which means the web interface and their custom binaries are somehow encrypted or more simply obfuscated and loaded at runtime in ram. At rest, the obfuscated files are called `/usr/web.bin`, `/usr/sbin.bin`, `/usr/apps.bin`. The executable responsabile for decrypting them to more simpler `tgz` archives is called `ap_monitor`. Ghidra sucessfully decompile this binary and the obfuscation mechanism is not very complicated and could reversed with not too much effort but there's proably no reason to do so.
|
||||
|
||||
|
||||
Since I was unable to find the manufacturer both on the package or anywhere else, i'll refer to it as `ZiKing` as it seems that's the name stated in their own proprietary config file. On Aliexpress, the same device is also often said to be made by `ANDDEAR`. Both do not seem to have any presence on the English internet.
|
||||
|
||||
The
|
||||
```
|
||||
FID="OEM"
|
||||
FLASH_ID="SPI"
|
||||
PCB="v1.0"
|
||||
PN="CPE46B"
|
||||
PT="AP"
|
||||
VER="4.3.7"
|
||||
VER1="4.3.7"
|
||||
RF_MODE="1T1R"
|
||||
WAN="0"
|
||||
EXT_PA="1"
|
||||
TRSW="1"
|
||||
SERVER_DOMAIN="www.ziking.net"
|
||||
DHCPD_EVER="0"
|
||||
IANA="37260"
|
||||
MAXNUM=4
|
||||
|
||||
## Raspberry PI GPIO with a SOIC8 CLIP
|
||||
####language
|
||||
CSS_STYLE="SHX46B"
|
||||
LANG="en"
|
||||
SUPPORT_LANG="en,zh"
|
||||
COUNTRYCODE="76"
|
||||
SUPPORT_COUNTRYCODE="76,156,276,392"
|
||||
####radio & vaps
|
||||
MAX_VAPS="8"
|
||||
MAX_RFS="1"
|
||||
#0: auto, 1:2.4G, 2-5.8G
|
||||
RF0_SUPPORT_FREQ="1"
|
||||
#RF1_SUPPORT_FREQ="0"
|
||||
|
||||
SUPPORT_AUTO_ACTIVE="0"
|
||||
#### product Type
|
||||
###0: FIT AP mode
|
||||
###1: WIFI CPE mode
|
||||
###2: LTE/3G CPE mode
|
||||
###3: Route mode
|
||||
####for UPNP
|
||||
MANUFACTURER="XIAN ZIKING NETWORK COMMUNICATIONS CO.,LTD."
|
||||
MANUFACTURERURL="http://www.ziking.net"
|
||||
MODELDESCRIPTION="Wireless Broadband Access Point / CPE"
|
||||
####
|
||||
PRODUCT_TYPE="1"
|
||||
SUPPORT_PRODUCT_TYPE="2,3"
|
||||
SUPPORT_WAN_MODE="251"
|
||||
SUPPORT_AUTH_MODE="63"
|
||||
SUPPORT_WLAN_MODE="7"
|
||||
SUPPORT_MAC_MAP="0"
|
||||
PRODUCT_ID="0"
|
||||
APSYSNEID="SYSNEIDatleast16chars1234567890123456"
|
||||
AP_NASID="NASIDatleast16chars1234567890123456"
|
||||
APSYSHOSTNAME="APNAMEatleast40chars1234567890123456789012345678901234567890"
|
||||
AP_LOCATION="shenzhen"
|
||||
AP_COVERAGETYPE="2"
|
||||
AP_DESCRIPRION="Customer Premise Equipment"
|
||||
AP_SOFT_VERDOR="ZiKing"
|
||||
AP_ORIG_VENDOR="ZiKing"
|
||||
AP_CPU="ar9331"
|
||||
CPU_SPEED="400000000"
|
||||
#it must be xxMB(type)
|
||||
AP_MEMORY="64MB(S29GL064M)"
|
||||
AP_FLASH="8MB(HY57V561620TP-H)"
|
||||
#max power, dbm
|
||||
AP_MAX_POWER="15"
|
||||
PCB0="SX933146B"
|
||||
BUS="AHB"
|
||||
SUPPORT_AC_CURL_MGR="0"
|
||||
AP_SERIALNUMBER=001122334455
|
||||
|
||||
```
|
||||
Note that the `64M` RAM value written there is wrong. This one has `32M` but it probably depends on the production batch.
|
||||
|
||||
The only thing actually existing, given that as of now the website shows a default page, is [their IANA assignment number](https://oidref.com/1.3.6.1.4.1.37260).
|
||||
|
||||
### Raspberry PI GPIO with a SOIC8 CLIP
|
||||
|
||||
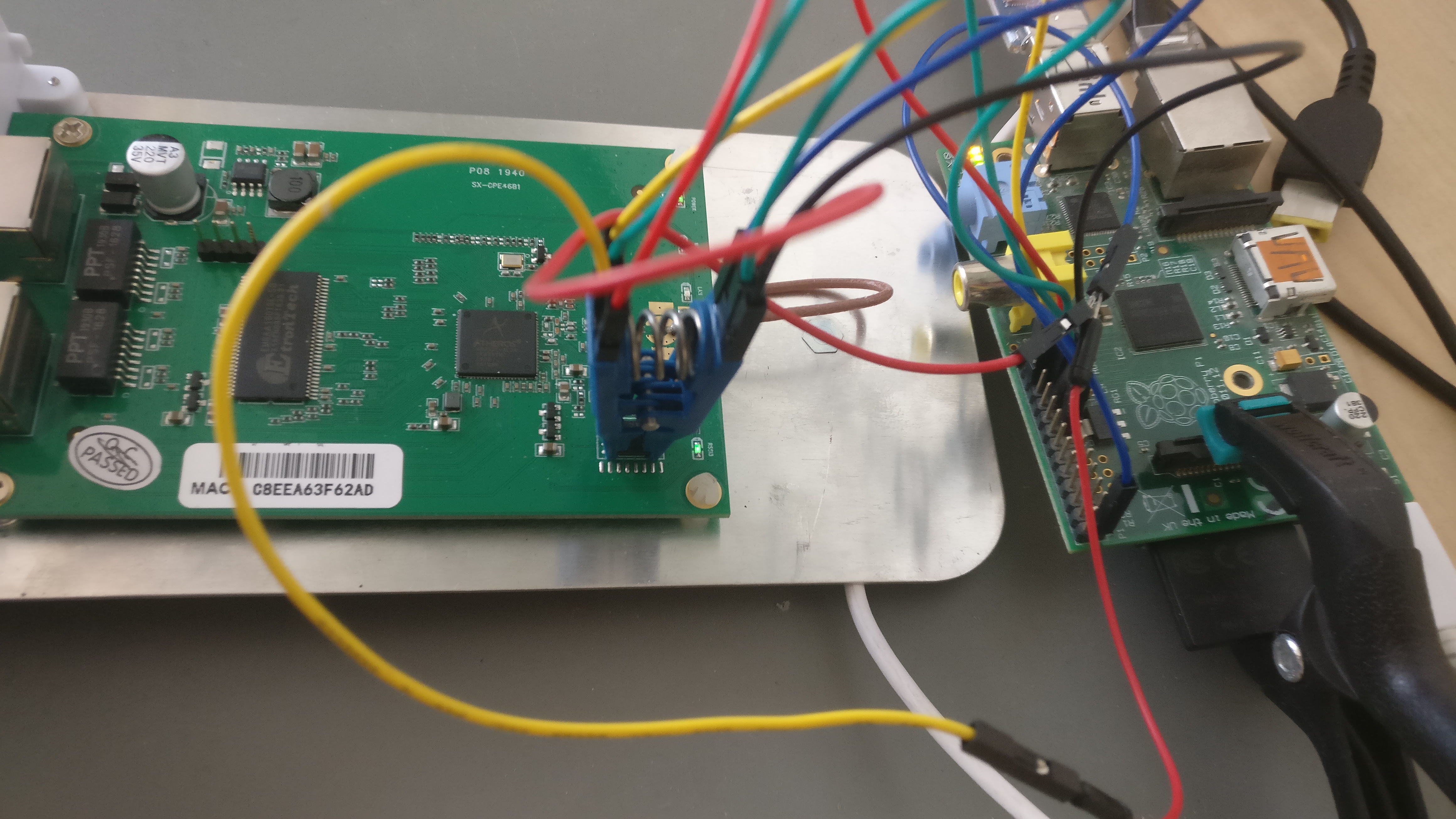
|
||||
|
||||
@ -167,7 +256,7 @@ From a root prompt on the Rpi
|
||||
```
|
||||
Check that all the checksums do match. In case they don't there's probably something wrong in the clip position or in the wiring. Remember that no pin should left floating even if it's not useful for the operation. /WP and /HOLD should be always connected to something like GND or VCC.
|
||||
|
||||
## Serial interface
|
||||
### Serial interface
|
||||
|
||||
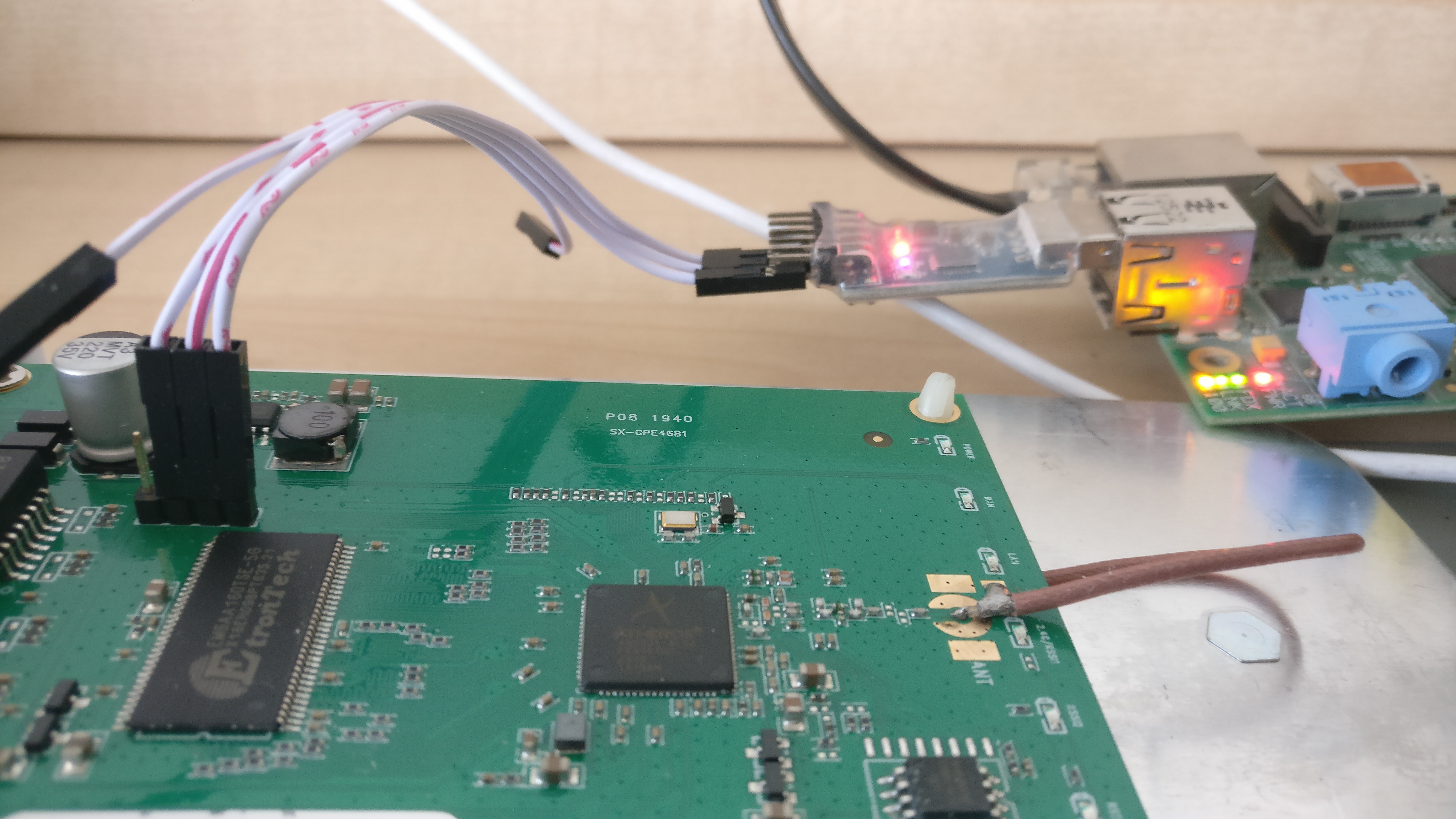
|
||||
|
||||
@ -177,4 +266,35 @@ Common softwares for serial communication are `minicom` and `screen`.
|
||||
|
||||
```
|
||||
# screen /dev/ttyUSB0 115200
|
||||
```
|
||||
```
|
||||
|
||||
## Porting
|
||||
### Partition layout
|
||||
The info learnet from `proc/mtd` are extremely useful.
|
||||
|
||||
* `mtd0 u-boot` is a 64K partition which contains the u-boot bootloader
|
||||
* `mtd1 u-boot-env` is a 64K partition containing the u-boot configuration
|
||||
* `mtd2 rootfs` is a jffs2 partition containing the actual image
|
||||
* `mtd3 uImage` is a squashfs kernel image
|
||||
* `mtd4 rootfs1` is a jffs2 partition containing a secondary image, probably used for recovery
|
||||
* `mtd5 NVRAM` is a 64K partition which contains a `tgz` for OEM system configuration files
|
||||
* `mtd6 ART` is a 64K partition [that contains calibration data for the radio chip](https://github.com/pepe2k/ar9300_eeprom)
|
||||
|
||||
The total size is of course 8192K. The partitions are not partitions in an EXT or NTFS sense. The data is just contiguos on the flash but the bootloader and the kernel are responsible for considering the different regions separate.
|
||||
|
||||
That's the reason because `cat` works and it is so simple to work with them.
|
||||
|
||||
Since for vanilla OpenWRT a custom partition for configuration is not needed, and two rootfs aren't useful and everything can be packed in a single partition with more space for packages and user data our target could be:
|
||||
|
||||
* `mtd0 u-boot` oeiginal image
|
||||
* `mtd1 u-boot-env` some values here needs to be modified
|
||||
* `mtd2 firmware` 8000K OpenWRT partition (`firmware` is the standard OpenWRT naming)
|
||||
* `mtd3 ART` original image
|
||||
|
||||
|
||||
On some other devices this is not needed because maybe the partition layotu already makes sense: ie there are no duplicate rootfs data. They are a bit easier to play with because in that case there's probably no need to manipulate the boot environment. Furthermore, building an image for flashing trough the OEM web interface might be not possible.
|
||||
|
||||
### U-Boot
|
||||
U-boot is an Open Source Bootloader mainly for embedded devices. While it is actively developed, the actual version depends on the SDK a vendor provides for its SoC.
|
||||
|
||||
Atheros, for `ar9330` seems to have used 1.4 as base, which is almost a decade old.
|
||||
Loading…
Reference in New Issue
Block a user